- Home >
- Web Help >
- SeekerWorks™ >
- Tables/Utilities - Security - Functions
Tables/Utilities - Security - Functions
The "List Of Users (for Functional Security)" screen (shown below) appears when you click the (Security - Functions) menu button. Once a person has been set up with a User-ID, you can use this screen to limit their access to the appropriate Functions they should have access to. Click on a User-ID to (Update) their security. The default is no access to any Functions other than the 'My' function screens.
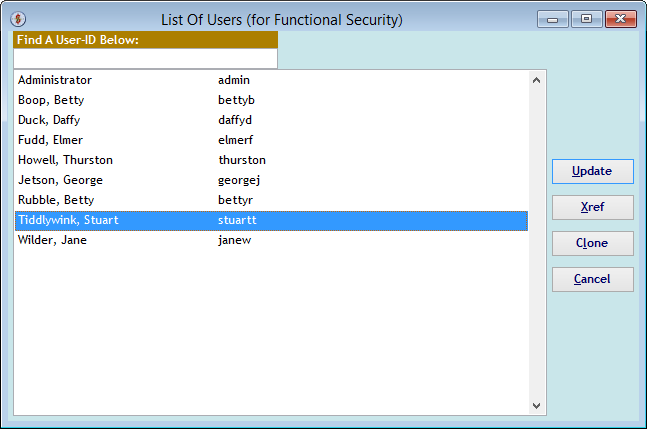
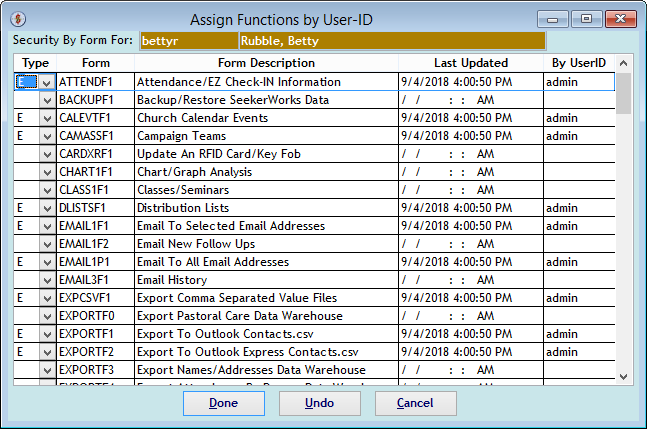
The "Assign Functions by User-ID" screen shows all of the current Functions and whether the User-ID has access to any of them.
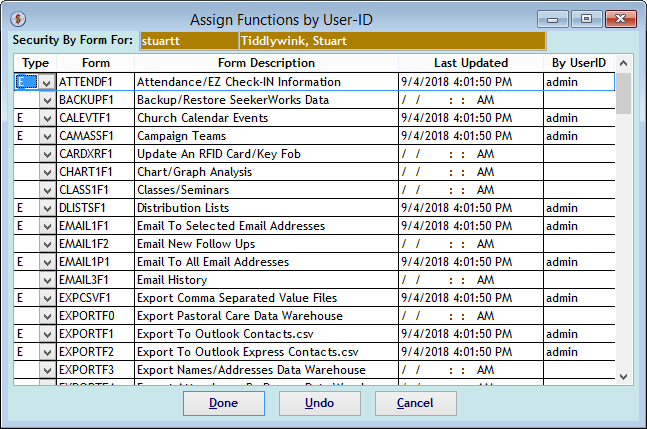
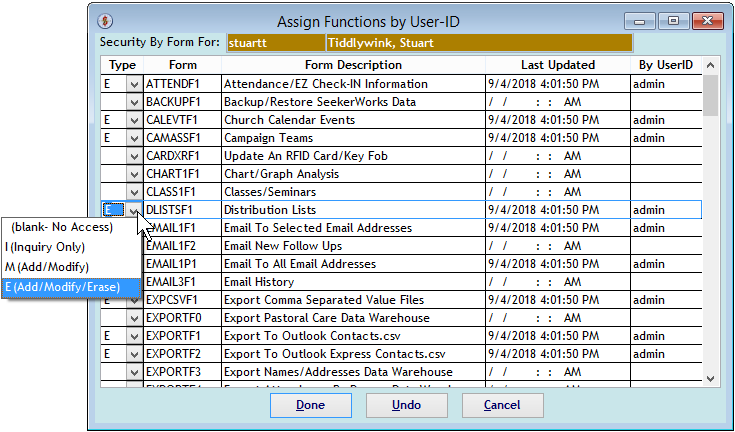
The "Assign Functions by User-ID, Access Types" screen further shows the type of access you can define for a User-ID. These include _ (blank- No Access), which is the default, I (Inquiry Only), M (Add/Modify) or E (Add/Modify/Erase).
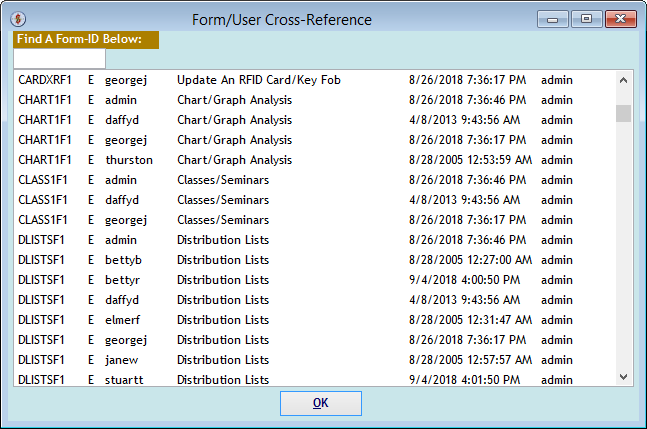
The "Form/User Cross-Reference" screen appears when you click the (Xref) button on the first screen. It shows each Function and each User-ID with access to it along with their type of access.
The "Clone A User's Functional Security Settings" screen appears when you <right-click> a User-ID on the first screen and click the (Clone) button. You can also use the (FROM User) or (To User) buttons to select different User-IDs.
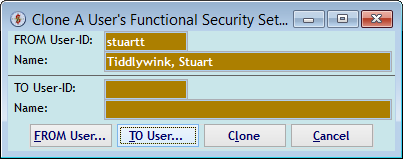
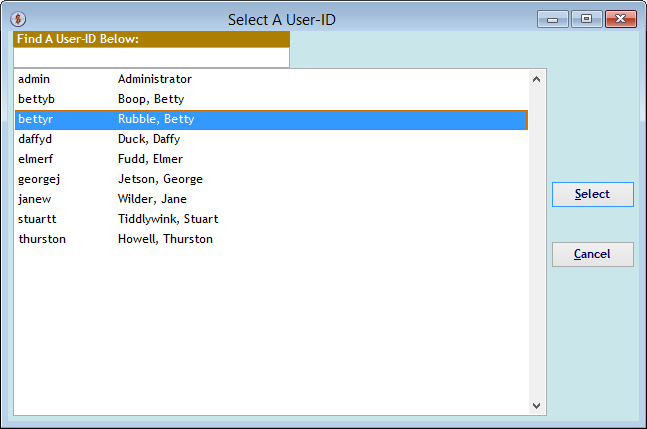
The "Select A User-ID" screen appears when you use the (FROM User) or (To User) buttons to select different User-IDs on the previous screen.
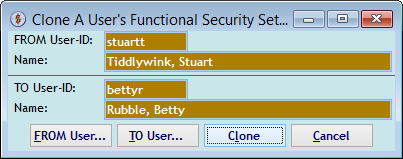
The "Clone A User's Functional Security Settings" screen re-appears with the User-IDs selected. Click (Clone) here to copy a person's security.
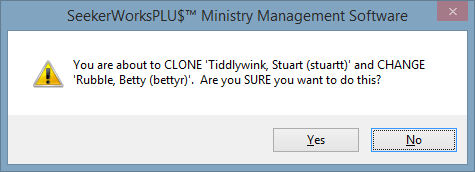
The "clone confirmation message box" confirms you are sure you want to change the 'To User-ID's Functional security to match that of the From User-Id's security.
The "Assign Functions by User-ID" screen now shows the 'To User-ID's Functional security settings.
Right side navigation links:
More Screens:
People:
Gifts/Pledges:
My Info/General Info:
Email/Labels/Merge:
Tables/Utilities:
Security - Functions